26 Jan 2026
 Planet KDE | English
Planet KDE | English
Qt Creator 18.0.2 released
We are happy to announce the release of Qt Creator 18.0.2!
This release fixes a range of smaller issues like the persistence of the "Always save files before build" option and an issue that occurred when using some custom toolchains with vcpkg. It also updates the wizard templates for the Qt Safe Renderer.
![]()
26 Jan 2026 11:01am GMT
25 Jan 2026
 Planet KDE | English
Planet KDE | English
Bouncy Ball will always bounce back
Bouncy Ball. A proper KDE 4 classic. Many hymns of praise have been sung about this lovable desktop extension. Do You Remember the KDE Bouncy Ball Widget? Fear not, OMG! Ubuntu! You will bounce again! The KDE Ball Widget Bounces Back to Life It's a widget that lets you play with a bouncy ball on...... Continue Reading →
25 Jan 2026 9:32am GMT
24 Jan 2026
 Planet KDE | English
Planet KDE | English
This Week in Plasma: fixing all the things
Welcome to a new issue of This Week in Plasma!
This week the Plasma team focused almost entirely on bug fixing. And let's let the results speak for themselves: we fixed 18 high and very high priority Plasma bugs, or 28% of all open ones! Lots of polishing for Plasma 6.6 to make it a great release.
Notable New Features
Plasma 6.7.0
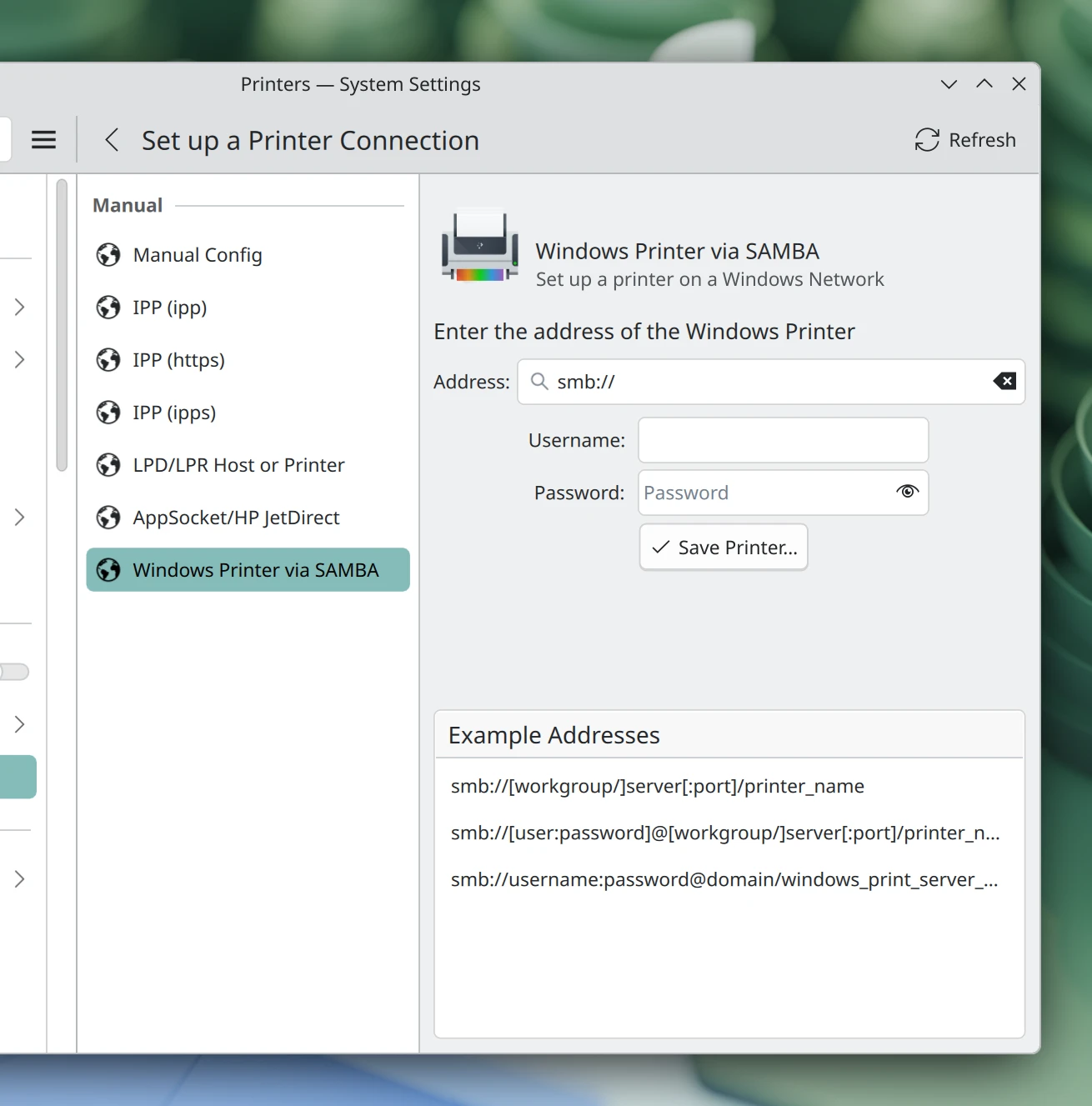
Added a dedicated setup UI for configuring shared printers on Windows networks. (Mike Noe, KDE Bugzilla #406211)
Notable UI Improvements
Plasma 6.6.0
Desktop switching and Present Windows shortcuts now use the Meta key by default for more consistent system-wide behavior. (Antti Savolainen, kwin MR #8597)
Plasma can now report printers' waste receptacle levels and notify users when they fill up. (Mike Noe, KDE Bugzilla #514525)
KRunner's buttons have been reorganized to be consistent with other Plasma widgets, making the interface feel more familiar and coherent. (Taras Oleksyn, plasma-workspace MR #6203)
Plasma 6.7.0
System Settings' Wi-Fi & Networking page now uses clearer Wi-Fi security labels, correctly showing WPA2 and WPA3 support for both Personal and Enterprise networks. (Lynne Megido, KDE Bugzilla #493238)
There are now keyboard shortcuts for switching virtual desktops and opening the Present Windows effect that use the Meta key, to be consistent with other globally-scoped keyboard shortcuts. (Antti Savolainen, KDE Bugzilla #508187)
Frameworks 6.23
Improved the visual fidelity of thumbnail images in open/save dialogs throughout Plasma and KDE apps. (Méven Car, KDE Bugzilla #489298)
Notable Bug Fixes
Plasma 6.5.6
Fixed an issue that could sometimes make KWin crash after periods of idleness. (Vlad Zahorodnii, KDE Bugzilla #513687)
Fixed an issue that would make Plasma crash when you disabled widgets in the System Tray and clicked the dialog window's "OK" button rather than the "Apply" button. (David Edmundson, KDE Bugzilla #478625)
Fixed an issue that could sometimes make KWin crash after repeatedly pressing the "Activate window demanding attention" shortcut (Meta+Ctrl+A by default) while multiple windows were demanding attention. (Vlad Zahorodnii, KDE Bugzilla #500748)
Fixed a common case where Plasma could crash after certain games crashed first. (David Edmundson, KDE Bugzilla #506562)
Fixed a common case where Plasma could crash when configured with a weather station from the Environment Canada source in its Weather Report widget. (Bohdan Onofriichuk, KDE Bugzilla #514553)
Fixed a case where changing the visibility of the Media Player widget in the System Tray while music was playing could make Plasma crash. (David Edmundson, KDE Bugzilla #514823)
Spectacle once again remembers the location where you last saved a screenshot the next time you save one. (Noah Davis, KDE Bugzilla #511649)
Fixed an issue causing 24" 16:9 aspect ratio monitors to get the wrong default resolution. (Anton Golubev, kwin MR #8681)
Plasma 6.6.0
Fixed a surprisingly common issue whereby KWin could sometimes crash when you frantically wiggled the pointer to try to stop a monitor from going to sleep. (Vlad Zahorodnii, KDE Bugzilla #487660)
Fixed a case where KWin could crash when you deleted a virtual desktop that still had windows on it. (Vlad Zahorodnii, kwin MR #8680)
Fixed another KWin crash, this one more random. (Xaver Hugl, kwin MR #8677)
Fixed a long-standing issue whereby tooltips opened by buttons in Plasma widget popups could move onto the panel and get stuck there after you closed the widget popups. (Marco Martin, KDE Bugzilla #475646)
Fixed an issue that made popups of panel widgets undesirably change their size when you moved their panel to an adjacent screen edge. (Christoph Wolk, KDE Bugzilla #512273)
Fixed an issue making certain sub-menus of Plasma widgets not have transparent backgrounds, which was especially visible with menu blurring turned on. (Marco Martin, KDE Bugzilla #513307)
Fixed an issue in the HDR calibrator tool that made long pieces of text overflow from their boxes. (Nate Graham and David Edmundson, KDE Bugzilla #514687)
Fixed an issue that made Plasma forget the IPSec certificate passwords of L2TP VPNs. (Mickaël Thomas, plasma-nm MR #460)
Fixed an issue causing apps launched using D-Bus activation to be omitted from System Monitor's Applications table. (Arjen Hiemstra, KDE Bugzilla #510235)
Fixed an issue in System Monitor that could make the Applications table's "Details" panel un-scrollable under certain circumstances. (Arjen Hiemstra, KDE Bugzilla #506150)
Fixed an issue in Discover that could sometimes make Flatpak apps' languages packages fail to get grouped with the apps. (Harald Sitter, KDE Bugzilla #513111)
Plasma 6.7.0
Fixed an issue that broke KRunner's Activities plugin from actually finding any activities. (Sam Morris, KDE Bugzilla #514000)
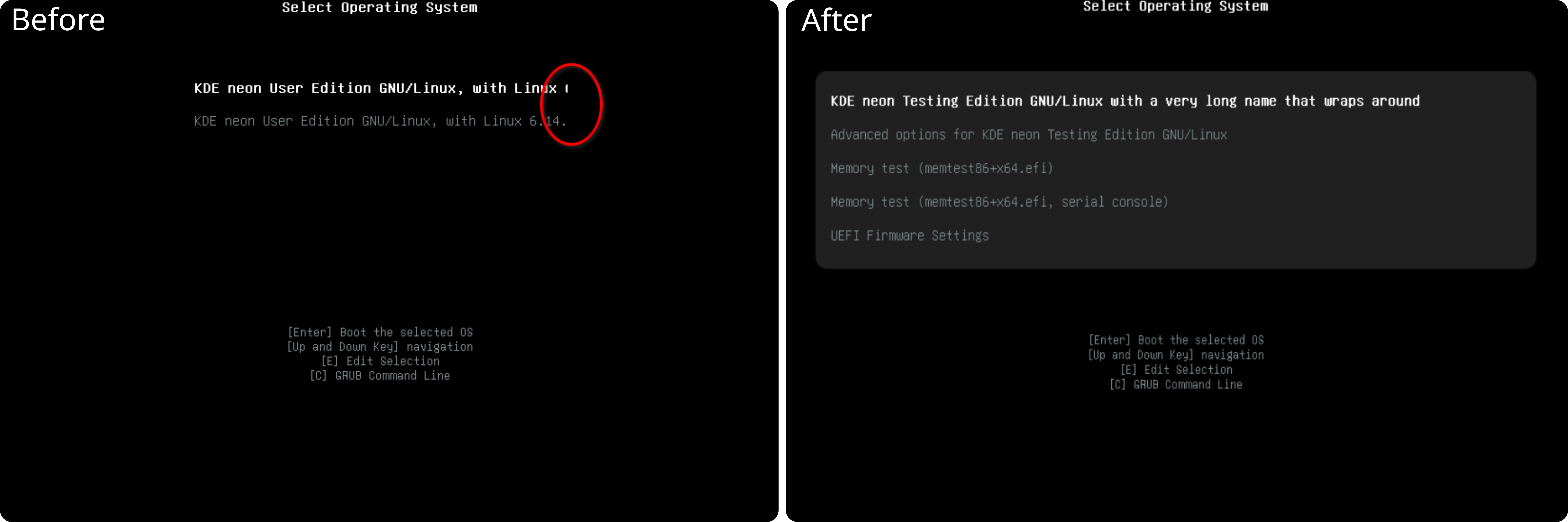
Fixed an issue that caused long boot menu entries to be cut off in the Breeze GRUB Menu styling. (Sébastien Bouchard, KDE Bugzilla #513107)
Frameworks 6.23
Fixed an issue that caused a large variety of crashes in Plasma and KDE apps related to devices appearing and disappearing. (Nicolas Fella, solid MR #232)
Fixed an issue making KWallet crash on OpenSUSE-based operating systems. (Nicolas Fella, KDE Bugzilla #490788)
Fixed an issue that broke the back button in Kirigami-based System Settings pages and apps when using a right-to-left language like Arabic or Hebrew and you went back and forward and then back again. (Youssef Al-Bor3y, KDE Bugzilla #511295)
Notable in Performance & Technical
Plasma 6.6.0
Plasma's system monitoring infrastructure received further fixes to improve OpenBSD support. (Rafael Sadowski, libksysguard MR #454)
PackageKit 1.3.4
Implemented support for DNF5 in PackageKit, which fixes a huge number of issues relevant to people using Discover on Fedora-based operating systems. (Neal Gompa, packagekit PR #931)
How You Can Help
"This Week in Plasma" still needs your help! Publishing these posts is time-consuming and needs community assistance to be sustainable. Right now there are two ways to help:
Work can be coordinated in the relevant Matrix room.
Beyond that, you can help KDE by directly getting involved in any other projects. Donating time is actually more impactful than donating money. Each contributor makes a huge difference in KDE - you are not a number or a cog in a machine! You don't have to be a programmer, either; many other opportunities exist.
You can also help out by making a donation! This helps cover operational costs, salaries, travel expenses for contributors, and in general just keep KDE bringing Free Software to the world.
To get a new Plasma feature or a bugfix mentioned here
Push a commit to the relevant merge request on invent.kde.org.
24 Jan 2026 12:03am GMT
23 Jan 2026
 planet.freedesktop.org
planet.freedesktop.org
Mike Blumenkrantz: Unpopular Opinion
A Big Day For Graphics
Today is a big day for graphics. We got shiny new extensions and a new RM2026 profile, huzzah.
VK_EXT_descriptor_heap is huge. I mean in terms of surface area, the sheer girth of the spec, and the number of years it's been under development. Seriously, check out that contributor list. Is it the longest ever? I'm not about to do comparisons, but it might be.
So this is a big deal, and everyone is out in the streets (I assume to celebrate such a monumental leap forward), and I'm not.
All hats off. Person to person, let's talk.
Power Overwhelming
It's true that descriptor heap is incredibly powerful. It perfectly exemplifies everything that Vulkan is: low-level, verbose, flexible. vkd3d-proton will make good use of it (eventually), as this more closely relates to the DX12 mechanics it translates. Game engines will finally have something that allows them to footgun as hard as they deserve. This functionality even maps more closely to certain types of hardware, as described by a great gfxstrand blog post.
There is, to my knowledge, just about nothing you can't do with VK_EXT_descriptor_heap. It's really, really good, and I'm proud of what the Vulkan WG has accomplished here.
But I don't like it.
What Is This Incredibly Hot Take?
It's a risky position; I don't want anyone's takeaway to be "Mike shoots down new descriptor extension as worst idea in history". We're all smart people, and we can comprehend nuance, like the difference between rb and ab in EGL patch review (protip: if anyone ever gives you an rb, they're fucking lying because nobody can fully comprehend that code).
In short, I don't expect zink to ever move to descriptor heap. If it does, it'll be years from now as a result of taking on some other even more amazing extension which depends on heaps. Why is this, I'm sure you ask. Well, there's a few reasons:
Code Complexity
Like all things Vulkan, "getting it right" with descriptors meant creating an API so verbose that I could write novels with fewer characters than some of the struct names. Everything is brand new, with no sharing/reuse of any existing code. As anyone who has ever stepped into an unfamiliar bit of code and thought "this is garbage, I should rewrite it all" knows too well, existing code is always the worst code-but it's also the code that works and is tied into all the other existing code. Pretty soon, attempting to parachute in a new descriptor API becomes rewriting literally everything because it's all incompatible. Great for those with time and resources to spare, not so great for everyone else.
Gone are image views, which is cool and good, except that everything else in Vulkan still uses them, meaning now all image descriptors need an extra pile of code to initialize the new structs which are used only for heaps. Hope none of that was shared between rendering and descriptor use, because now there will be rendering use and descriptor use and they are completely separate. Do I hate image views? Undoubtedly, and I like this direction, but hit me up in a few more years when I can delete them everywhere.
Shader interfaces are going to be the source of most pain. Sure, it's very possible to keep existing shader infrastructure and use the mapping API with its glorious nested structs. But now you have an extra 1000 lines of mapping API structs to juggle on top. Alternatively, you can get AI to rewrite all your shaders to use the new spirv extension and have direct heap access.
Performance
Descriptor heap maps closer to hardware, which should enable users to get more performant execution by eliminating indirection with direct heap access. This is great. Full stop.
…Unless you're like zink, where the only way to avoid shredding 47 CPUs every time you change descriptors is to use a "sliding" offset for descriptors and update it each draw (i.e., VK_DESCRIPTOR_MAPPING_SOURCE_HEAP_WITH_PUSH_INDEX_EXT). Then you can't use direct heap access. Which means you're still indirecting your descriptor access (which has always been the purported perf pain point of 1.0 descriptors and EXT_descriptor_buffer). You do not pass Go, you do not collect $200. All you do is write a ton of new code.
Opinionated Development
There's a tremendous piece of exposition outlining the reasons why EXT_descriptor_heap exists in the proposal. None of these items are incorrect. I've even contributed to this document. If I were writing an engine from scratch, I would certainly expect to use heaps for portability reasons (i.e., in theory, it should eventually be available on all hardware).
But as flexible and powerful as descriptor heap is, there are some annoying cases where it passes the buck to the user. Specifically, I'm talking about management of the sampler heap. 1.0 descriptors and descriptor buffer just handwave away the exact hardware details, but with VK_EXT_descriptor_heap, you are now the captain of your own destiny and also the manager of exactly how the hardware is allocating its samplers. So if you're on NVIDIA, where you have exactly 4096 available samplers as a hardware limit, you now have to juggle that limit yourself instead of letting the driver handle it for you.
This also applies to border colors, which has its own note in the proposal. At an objective, high-view level, it's awesome to have such fine-grained control over the hardware. Then again, it's one more thing the driver is no longer managing.
I Don't Have A Better Solution
That's certainly the takeaway here. I'm not saying go back to 1.0 descriptors. Nobody should do that. I'm not saying stick with descriptor buffers either. Descriptor heap has been under development since before I could legally drive, and I'm certainly not smarter than everyone (or anyone, most likely) who worked on it.
Maybe this is the best we'll get. Maybe the future of descriptors really is micromanaging every byte of device memory and material stored within because we haven't read every blog post in existence and don't trust driver developers to make our shit run good. Maybe OpenGL, with its drivers that "just worked" under the hood (with the caveat that you, the developer, can't be an idiot), wasn't what we all wanted.
Maybe I was wrong, and we do need like five trillion more blog posts about Vulkan descriptor models. Because releasing a new descriptor extension is definitely how you get more of those blog posts.
23 Jan 2026 12:00am GMT
21 Jan 2026
 planet.freedesktop.org
planet.freedesktop.org
Simon Ser: Status update, January 2026
Hi!
Last week I've released Goguma v0.9! This new version brings a lot of niceties, see the release notes for more details. New since last month are audio previews implemented by delthas, images for users, channels & networks, and usage hints when typing a command. Jean THOMAS has been hard at work to update the iOS port and publish Goguma on AltStore PAL.
It's been a while since I've started a NPotM, but this time I have something new to show you: nagjo is a small IRC bot for Forgejo. It posts messages on activity in Forgejo (issue opened, pull request merged, commits pushed, and so on), and it expands references to issues and pull requests in messages (writing "can you look at #42?" will reply with the issue's title and link). It's very similar to glhf, its GitLab counterpart, but the configuration file enables much more flexible channel routing. I hope that bot can be useful to others too!
Up until now, many of my projects have moved to Codeberg from SourceHut, but the issue tracker was still stuck on todo.sr.ht due to a lack of a migration tool. I've hacked together srht2forgejo, a tiny script to create Forgejo issues and comments from a todo.sr.ht archive. It's not perfect since the author is the migration user's instead of the original one, but it's good enough. I've now completely migrated all of my projects to Codeberg!
I've added a server implementation and tests to go-smee, a small Go library for a Web push forwarding service. It comes in handy when implementing Web push receivers because it's very simple to set up, I've used it when working on nagjo.
I've extended the haproxy PROXY protocol to add a new client certificate TLV to relay the raw client certificate from a TLS terminating reverse proxy to a backend server. My goal is enabling client certificate authentication when the soju IRC bouncer sits behind tlstunnel. I've also sent patches for the kimchi HTTP server and go-proxyproto.
Because sending a haproxy patch involved git-send-email, I've noticed I've started hitting a long-standing hydroxide signature bug when sending a message. I wasn't previously impacted by this, but some users were. It took a bit of time to hunt down the root cause (some breaking changes in ProtonMail's crypto library), but now it's fixed.
Félix Poisot has added two new color management options to Sway: the color_profile command now has separate gamma22 and srgb transfer functions (some monitors use one, some use the other), and a --device-primaries flag to read color primaries from the EDID (as an alternative to supplying a full ICC profile).
With the help of Alexander Orzechowski, we've fixed multiple wlroots issues regarding toplevel capture (aka. window capture) when the toplevel is completely hidden. It should all work fine now, except one last bug which results in a frozen capture if you're unlucky (aka. you loose the race).
I've shipped a number of drmdb improvements. Plane color pipelines are now supported and printed on the snapshot tree and properties table. A warning icon is displayed next to properties which have only been observed on tainted or unstable kernels (as is usually the case for proprietary or vendor kernel modules with custom properties). The device list now shows vendor names for platform devices (extracted from the kernel table). Devices using the new "faux" bus (e.g. vkms) are now properly handled, and all of the possible cursor sizes advertised via the SIZE_HINTS property are now printed. I've also done some SQLite experiments, however they turned out unsuccessful (see that thread and the merge request for more details).
delthas has added a new allow_proxy_ip directive to the kimchi HTTP server to mark IP addresses as trusted proxies, and has made it so Forwarded/X-Forwarded-For header fields are not overwritten when the previous hop is a trusted proxy. That way, kimchi can be used in more scenario: behind another HTTP reverse proxy, and behind a TCP proxy which doesn't have a loopback IP address (e.g. tlstunnel in Docker).
See you next month!
21 Jan 2026 10:00pm GMT
Christian Schaller: Can AI help ‘fix’ the patent system?
So one thing I think anyone involved with software development for the last decades can see is the problem of "forest of bogus patents". I have recently been trying to use AI to look at patents in various ways. So one idea I had was "could AI help improve the quality of patents and free us from obvious ones?"
Lets start with the justification for patents existing at all. The most common argument for the patent system I hear is this one : "Patents require public disclosure of inventions in exchange for protection. Without patents, inventors would keep innovations as trade secrets, slowing overall technological progress.". This reasoning is something that makes sense to me, but it is also screamingly obvious to me that for it to hold true you need to ensure the patents granted are genuinely inventions that otherwise would stay hidden as trade secrets. If you allow patents on things that are obvious to someone skilled in the art, you are not enhancing technological progress, you are hampering it because the next person along will be blocking from doing it.
So based on this justification the question then becomes does for example the US Patents Office do a good job filtering out obvious patents? And I believe the answer is "No they don't". Having been working in the space of software for many decades now it is very clear to me that the patent office do very little to avoid patents getting approved for obvious things. And there are many reasons for why that happens I think. First of all if you are an expert in a field you would likely not be working as a case worker in the patent office, no disrespect for the people working there, but for instance if you are a really good software engineer there are much better paying options to be found elsewhere, same goes for medical researchers for example. So we have people who have limited understanding of the field of the patent trying to evaluate if the patent is obvious or not.
Secondly the patent office is not really incentivized to deny patents as they are a self funded entity and their 'success' and revenue is based on how many patent applications are submitted. So the lower the bar of approval, the more patents applications get submitted and thus the patent office makes more money and is more "successful". This is a problem, but maybe if we fix the first issue I mention it is maybe possible to reduce the impact of this second issue.
So what can AI do to help here? It can help patent reviewers at the patent office with evaluating patents for obviousness due to having been trained on these fields. If we required every patent applied for to be run through a AI engine for review then the patent office reviewer would have to justify why he or she believes something is non-obvious after the AI has looked at it and concluded it is not. My assumption would be that they would very rarely do so.
To test out this I decided to ask Gemini to review a H264 video patent that is still valid and which has been used in litigation before, to see if it could do a decent job of reviewing the patent application and judge if this is a true invention or not. Here is what Gemini came up with.
US Patent 7,916,782 (Samsung Electronics) is one of the most famous "battleground" patents in the history of smartphone litigation. It has been asserted against Apple, Huawei, and others.
It covers a specific part of the H.264 standard known as CAVLC (Context-Adaptive Variable Length Coding).
The Patent: US 7,916,782 : Method and apparatus for video coding and decoding The Mechanism: Efficiently coding the count of zero-valued pixels in a video block ("TotalZeros").
The Problem
In video compression, you divide the image into small 4×4 pixel blocks. After processing (transform and quantization), most of the 16 pixels in the block end up being zero. You only have a few non-zero numbers left.
Goal: You need to tell the decoder how many zeros are in the block so it can reconstruct the empty space.
Constraint: You already told the decoder how many non-zero coefficients exist (let's say you have 5 non-zeros).
The "Invention" The patent claims a method where the encoder selects a specific lookup table (VLC table) to encode the "TotalZeros" value, and-crucially-this selection is based on the number of non-zero coefficients (TotalCoeff) that were just processed. If TotalCoeff is 1, use Table A (allows for many zeros).If TotalCoeff is 10, use Table B (allows for fewer zeros).
The "Skilled Engineer" Test
Imagine you are a video coding engineer in 2002. You are tasked with compressing the "TotalZeros" value. Here is the logical deduction chain you would inevitably follow:
- The Constraint Check (Basic Math)
Engineer's Thought: "I am working with a 4×4 block. That's 16 pixels total."
Engineer's Thought: "I just transmitted the number of non-zero pixels. Let's say there are 5 non-zeros.
Deduction: "Therefore, the maximum number of zeros possible is 16−5=11." - The Optimization (Common Sense)
Engineer's Thought: "I need a Huffman table (lookup table) to compress the TotalZeros value."
Engineer's Thought: "Should I use a generic table that goes from 0 to 16?"
Deduction: "No, that's wasteful. I know for a fact the value cannot be 12, 13, 14, 15, or 16. If I use a table that includes those impossible numbers, I'm wasting bits on shorter codes for values that will never happen." - The Solution (The "Invention")
-
Engineer's Thought: "I should use a smaller, custom table that only contains values 0 through 11."
Engineer's Thought: "Actually, I should just make a different table for every possible number of non-zeros. If I have 15 non-zeros, the only possible zero count is 1. I don't even need a table for that; it's implicit!"The Verdict: Valid or Broken?
Engineer's View (Obvious): This is not an invention; it is constraint propagation. If you have a container of capacity 16, and you fill it with 5 rocks, it is "obvious" that the remaining space for air is 11. Creating a table sized to "11" isn't a creative spark; it is the mathematical consequence of the block size. To an engineer, failing to do this would be incompetence, not a design choice.Patent Office View (Novel): The USPTO granted this because the patent didn't just claim "optimizing tables." It claimed the specific structure of the solution: Check TotalCoeff.If TotalCoeff is 1, select Table_1. If TotalCoeff is 2, select Table_2. …and so on. Because no prior paper had explicitly written down "Use these specific tables in this specific order for H.264," it was deemed novel.
Conclusion US 7,916,782 is a prime example of the "broken" system because it effectively patents arithmetic efficiency. By granting a monopoly on the logic "Use a small table when you have small space," the patent office allowed Samsung to assert ownership over the only logical way to implement the H.264 standard efficiently. An engineer trying to solve this problem without seeing the patent would essentially be forced to "re-invent" it, because the math leaves no other optimal path.
Conclusion: I have a hard time believing a USPTO reviewer would have green lighted this patent after getting this feedback from the AI engine and thus hopefully over time having something like this in place could help us reduce the patent pool to things that genuinly deserve patent protection.
21 Jan 2026 6:35pm GMT