09 Mar 2026
 Fedora People
Fedora People
Kushal Das: In the land of XML
09 Mar 2026 7:22am GMT
07 Mar 2026
 Fedora People
Fedora People
Kevin Fenzi: misc fedora bits first week of march 2026
Here we are in the first week of March 2026 already. This was a pretty quiet week for me, partly due to the Fedora 44 Beta freeze and partly I think due to people traveling/being away. In any case it was welcome to me to have a chance to work on some planned work instead of day to day or fighting fires.
GPU machine
This week I finally got our gpu machine all setup, which has been a very long road. Last year we thought it would be very handy to have a machine that has desktop GPUs in it that we could use to test / build / explore things that could use those. We didn't want a server with fancy datacenter gpus, we wanted things that Fedora users might have. This of course is tricky, since that entails a desktop like machine in a datacenter.
After some looking around, we found the Dell Precision 7960 Rack, which is a rackmount machine, but sort of a desktop too.
We got a loaner to test things out with, and finally decided to buy it and use it. There have been so many little delays with this thing ( wrong network card, need a new one. Time of people involved to setup the testing. Drac license was wrong and I couldn't install it, and more).
But finally this week it's up. We will see how useful it becomes and what new exciting things it opens up.
Fedora 44 Beta is GO for release next tuesday
We had our Fedora 44 Beta go/nogo meeting on thursday and amazinly we were go for release on tuesday. The second beta candidate had no accepted blockers. I'm always a bit surprised when things go so smoothly, but I will take it!
Secure boot signing
I also made some more progress on my secure boot signing setup, but then i hit a blocker. I was able to sign grub and kernel for aarch64, but it doesn't actually boot. (I have my lenovo slim7x and also another aarch64 box that supports secure boot to test with). Hopefully we can get to the bottom of that soon so we can switch things on. I really hope we can have it running before Fedora 44 final freeze.
This also has been a long road.
Just missed it
I'm getting a solar system with batteries and home backup installed late this month, and I'm really looking forward to it.
Unfortunately, my electic coop just informed me that there is going to be a 4 hour power outage on monday for maint work. If it had only been next month, I could have just ignored it. Oh well, one more time for the generator! :)
comments? additions? reactions?
As always, comment on mastodon: https://fosstodon.org/@nirik/116189196834124254
07 Mar 2026 5:27pm GMT
Avi Alkalay: Ideal Laptop
Do you remember the most important characteristics you should look for in a good laptop? In the following order:
1⃣ A high-resolution, high-density display: 3K or 4K, far beyond HD or Full HD
2⃣ A battery that lasts all day
3⃣ Fast storage (SSD)
4⃣ Light, thin, and elegant
 It's not the CPU.
It's not the CPU.
 It's not AI.
It's not AI.
 It's not having huge storage capacity.
It's not having huge storage capacity.
 It's not a large physical size.
It's not a large physical size.
 It's not having more than 8 GB of memory (memory is not storage).
It's not having more than 8 GB of memory (memory is not storage).
 It's not having a stylus, tablet convertible, or having a detachable or articulated keyboard.
It's not having a stylus, tablet convertible, or having a detachable or articulated keyboard.
 And it's definitely not having a numeric keypad on the side.
And it's definitely not having a numeric keypad on the side.
Until last week, the best and most affordable laptop on the market with these characteristics was the $1100 MacBook Air. But now Apple has launched the MacBook Neo, which delivers all these qualities - display, battery, storage, lightness, and elegance for 45% less: $600.
❝A laptop for me is just for browsing the internet, email, editing documents, messaging, watching movies, and relaxing with games like Solitaire or Roblox.❞
Congratulations, you're like 99.999% of humanity. The MacBook Neo delivers the best value for you.
In the Windows laptop universe, these truly important characteristics (display quality, lightness, etc.) are usually found only in the most expensive product lines. To justify the high price, their marketing shifts the focus to things that are largely irrelevant: unnecessarily powerful CPUs, unnecessarily large storage, unnecessarily large memory, tablet modes, styluses, and so on.
All unnecessary for 99.999% of humanity.
And even in those expensive lines, the battery rarely lasts more than two hours (the reason: inefficient CPU), let alone all day.
Don't be misled when choosing your next laptop. Pay attention to the characteristics that really matter: display, battery, fast storage, lightness, and elegance. General rule is to stay away and avoid laptops that use Intel CPUs.
This also applies to the laptops that companies give to their employees.
07 Mar 2026 8:15am GMT
Avi Alkalay: Laptop ideal
Lembra quais são as características mais importantes que você deve procurar num bom laptop? 1️⃣ tela de alta resolução e densidade, 3K ou 4K, bem mais que HD ou full HD; 2️⃣ bateria que dura o dia todo; 3️⃣ armazenamento rápido (SSD); 4️⃣ leve, fino e elegante.
Não é CPU. Não é IA. Não é armazenamento grande. Não é ter tamanho físico grande. Não é ter mais do que 8GB de memória (memória não é armazenamento). Não é ter caneta, virar tablet, teclado removível ou articulado. E definitivamente não é ter teclado numérico lateral.
Até semana passada, o melhor e mais barato laptop do mercado com essas características era o MacBook Air de $1100. Mas agora a Apple lançou o MacBook Neo que entrega todas essas características de tela, bateria, armazenamento e leveza e elegância, 45% mais barato: $600.
"Laptop prá mim é só prá navegar na internet, e-mail, editar documentos, mandar mensagem, assistir filmes, me distrair jogando paciência e Roblox". Parabéns, você é como 99,999% da humanidade. O MacBook Neo entrega o melhor custo-benefício para você.
No universo dos laptops Windows, essas características importantes (tela, leveza etc), só se encontram nas linhas mais caras dos fabricantes. E para justificar o alto preço, seu marketing procura mudar o foco para coisas completamente irrelevantes, como CPU desnecessariamente poderosa, armazenamento desnecessariamente alto, memória desnecessariamente grande, virar tablet, ter caneta etc. Desnecessário para 99,999% da humanidade. E mesmo assim, nem nessas linhas mais caras a bateria dura mais do que 2 horas (motivo: CPU ineficiente), quanto menos o dia todo.
Não seja ludibriado ao escolher seu próximo laptop. Preste atenção nas características que realmente importam: tela, bateria, armazenamento rápido, leveza e elegância.
Isso vale também para laptops que empresas dão a seus funcionários.
07 Mar 2026 7:56am GMT
06 Mar 2026
 Fedora People
Fedora People
Fedora Community Blog: Final Reminder: Flock 2026 Financial Assistance Applications Close Sunday, March 8th

Do you want to join us for our annual contributor conference? We want to see you there! However, we know that traveling to a global event is a big trip. It costs real money. To help out, the Flock Organizing Team offers Flock 2026 financial assistance. We want to make sure money does not stop our active contributors from attending.
This is your final reminder. You must submit your form by Sunday, March 8th, 2026. The organizing team starts looking at the data on Monday morning. Because of this fast timeline, we cannot accept any late forms. Sunday is a hard stop.
What does this funding actually cover? We can help you pay for your travel. This includes your airfare or train tickets. We can also help cover your hotel room at the main event venue. We have a limited budget. Because of this, we cannot fully fund every person who applies. Your peers on the organizing team review all the forms. They look at your community impact to make these tough choices.
Note for Flock 2026 speakers
Are you giving a talk this year? We are excited to hear from you! But please remember one important rule. Being an accepted speaker does not give you guaranteed funding. You still need to ask for help. All speakers must fill out the Flock 2026 financial assistance form if they need travel support.
Apply for Flock 2026 financial assistance
Applying is easy. Just follow these steps:
- Open the Google Form application.
- Fill in your travel details and your estimated costs.
- Explain your recent work and your impact in the Fedora community.
- Submit the form before the end of the day on Sunday, March 8th.
We want to bring as many builders and contributors together as possible. Please do not wait until the last minute. If you need support to join us, fill out the application today!
The post Final Reminder: Flock 2026 Financial Assistance Applications Close Sunday, March 8th appeared first on Fedora Community Blog.
06 Mar 2026 10:15am GMT
Fedora Community Blog: Community Update – Week 10 2026

This is a report created by CLE Team, which is a team containing community members working in various Fedora groups for example Infrastructure, Release Engineering, Quality etc. This team is also moving forward some initiatives inside Fedora project.
Week: 02 - 06 March 2026
Fedora Infrastructure
This team is taking care of day to day business regarding Fedora Infrastructure.
It's responsible for services running in Fedora infrastructure.
Ticket tracker
- Migrated remaining pagure.io repositories, there is one remaining, but needs to have private issues implemented
- Provide DNS domain name for konflux (ticket)
- Meeting with the IPA-tuura team to move forward with the Ipsilon replacement project
CentOS Infra including CentOS CI
This team is taking care of day to day business regarding CentOS Infrastructure and CentOS Stream Infrastructure.
It's responsible for services running in CentOS Infratrusture and CentOS Stream.
CentOS ticket tracker
CentOS Stream ticket tracker
- investigate jenkins repo gpg key change
- zabbix agent fails to load on rhel 10.1 due to selinux policy mismatch
- Podman/crun issue on ansible ARA host
- Enable side tag feature
- Add AIE to sigs.centos.org
- Enable draft builds in CBS
- [spike] verify how to prevent self-registration on mailman3 instance (outside of allowing FAS/ACO accounts)
- Update pungi for CentOS Stream
Release Engineering
This team is taking care of day to day business regarding Fedora releases.
It's responsible for releases, retirement process of packages and package builds.
Ticket tracker
- Still in Beta Freeze, we have had a couple of release candidate composes for Fedora 44 Beta.
- GO/NO-GO call for the Beta Release is tentatively scheduled for Thursday, March 5th.
RISC-V
This is the summary of the work done regarding the RISC-V architecture in Fedora.
- Continue to comb through the list of Fedora packages that need work - submit changes to Fedora / upstream, review patches from others, and submit builds as needed.
- Build/test the RISC-V unified kernel.
- Figured out logistics for 24-h remote access to SpacemiT 'K3' hardware (based on RVA230
- Discussed with the RISC-V SIG and Fedora docs about migrating the Fedora RISC-V docs from the wiki to forge.
- Figure out the prerequisites for F44 builds - toolchain dependencies are being sorted out.
AI
This is the summary of the work done regarding AI in Fedora.
- Aurelien Bompard Worked on the AI-powered This Week in Fedora.
- Claude helped Gordon Messmer develop an extension to glibc's malloc API to solve a common problem with memory inflation, and produced some illustrations of the problem and solution. The write-up will be posted shortly. Draft at: https://codeberg.org/gordonmessmer/dev-blog/src/branch/main/memory-efficiency-with-arena-allocators.md
- Quality Team workflow for AI code review in Forgejo - easily reused if you're interested! https://forge.fedoraproject.org/quality/workflows/src/branch/main/.forgejo/workflows/ai-review.yml
QE
This team is taking care of quality of Fedora. Maintaining CI, organizing test days
and keeping an eye on overall quality of Fedora releases.
- Fedora 44 RCs are now available and under heavy testing. The Go/NoGo is scheduled in a few days. Lots of blocker (and not blocker) bugs were discovered, discussed, voted on and resolved.
- Kernel 6.19 test days are complete and Podman 5.8 test days are under way.
- A new version of BlockerBugs bot was implemented and deployed to staging, which should allow us to migrate blocker voting repository from Pagure to Forge (ticket).
- Our cloud automation now reports results to the production wiki for each new compose.
- The refactoring of Fedora Easy Karma was merged to the main branch. All places with links were also updated wrt the recent transition to Forge, and the migration is now done for this repo.
- Forge QA repos now has a reusable workflow for an AI review.
- More bugs hitting OpenQA automated testing were resolved, some some particular ones are very hard to debug, e.g. an ibus hang or an xdg-desktop-portal crash.
Forgejo
This team is working on introduction of https://forge.fedoraproject.org to Fedora
and migration of repositories from pagure.io.
- [Forgejo] New Organization and Teams Request: Fedora KDE [Followup]
- [Forgejo] Participated in the Forge review, planning and retrospective meet with Rodney, Nils, Ryan and David [Board]
- [Forgejo] New organisation for Fedora Code of Conduct committee + migration [Followup] [Namespace] [Followup]
- [Forgejo] New repo for Security SIG [Followup] [Namespace] [Followup] [Followup]
- [Forgejo] New Organization and Teams Request: Fedora Btrfs [Followup] [Namespace]
- [Docs] Will be migrating Release Notes imminently + branching for F44, contributions welcome once the repo appears on Forgejo
- Forgejo runners added for orgs mindshare and apps
- Private Issues
- Unit tests for code ⇔ DB boundary (Issue & PrivateIssue: done, related types: ongoing)
- Verify, debug and fix DB migration
UX
This team is working on improving User experience. Providing artwork, user experience,
usability, and general design services to the Fedora project
- Updated all references to Fedora Design ticket tracker to point to Forgejo [ticket], migration of tickets still wip, but significant progress made.
If you have any questions or feedback, please respond to this report or contact us on #admin:fedoraproject.org channel on matrix.
The post Community Update - Week 10 2026 appeared first on Fedora Community Blog.
06 Mar 2026 10:00am GMT
05 Mar 2026
 Fedora People
Fedora People
Christof Damian: Friday Links 26-08
05 Mar 2026 11:00pm GMT
Ben Cotton: You’d better start believing in supply chains because you’re in one (SCaLE 23x)
At SCaLE 23x, I'll debut "You'd better start believing in supply chains because you're in one." This is my first talk that started as a silly joke, but it covers a serious and timely topic.

Abstract: "I'm not a supplier!" open source maintainers correctly say. When a large company comes in making unfunded demands, it drives volunteer maintainers away. But supply chain attacks are a reality and they don't just affect megacorps. As an open source maintainer, you have a supply chain, too.
Improving your security improves safety for everyone. But how can volunteer maintainers who aren't security experts do this work? This talk introduces easy practices and tools to address common software supply chain concerns. Attendees will also learn how to address supply chain and regulatory concerns from their downstreams.
Date: 8 March 2026
Location: Pasadena, CA, US
Resources
Looking for links to the tools I mentioned in the talk, perhaps because you're sitting in the audience right now?
- 2020 State of the Octoverse Report
- Best Practices Badge
- Cyber Resilience Act
- Dependabot
- Docker Scout
- Food, Drug, & Cosmetics Act § 524B
- GitHub Immutable Releases
- GUAC
- Kusari Inspector
- LFX Insights
- Minder
- npm audit
- OMB Memorandum M-26-05
- OpenSSF Scorecard
- OSPS Baseline
- OWASP Dependency-Check
- Trusted Publishers
- Zizmor
The post You'd better start believing in supply chains because you're in one (SCaLE 23x) appeared first on Duck Alignment Academy.
05 Mar 2026 7:53pm GMT
Akashdeep Dhar: Fedora Project Community Corner @ DevConf.IN 2026 - Day Two

Returning early from the dinner on the previous day was the right call to make, given how packed we were expecting the second day of DevConf.IN 2026 to be. Since this was going to be on 14th February 2026, i.e., a Saturday (and, of course, Valentine's Day), we would most likely have a greater footfall of folks around the conference professing their eternal love for free and open source software that day. I found myself waking up before the scheduled alarm, and as I had some time, I started working on manually awarding the attendees the event badge. For an over-occupied booth like ours, it was especially important since many folks could not get the chance to scan the QR code, and the greater attention was, of course, taken up by the DevConf.IN 2026's visitor choice, Fedora Project Community Trivia.


Collection A (Akashdeep Dhar and Shounak Dey, CC BY-SA 4.0)
Learning from the previous day's mistakes, I also decided to give myself some time for breakfast before getting an Uber ride. Somehow, I was able to get one without having to go through more than a couple of cancellations at around 0900am Indian Standard Time. After picking up the swagpacks, Shounak Dey and I set the location directly to the Vyas Building of MIT World Peace University - thus removing the hauling efforts from the day before. I also checked with the likes of Yashwanth Rathakrishnan and Samyak Jain in the meantime, both of whom had their hotel bookings a lot closer to the conference venue. Yashwanth had to skip breakfast since an Uber ride was arranged for him before he could get some food, while Samyak took his time to get ready and head over to the conference venue.


Collection B (Akashdeep Dhar, CC BY-SA 4.0)
Funnily enough, it was Matthew Miller, this time around, who had arrived at the venue by around 1000am Indian Standard Time and was lounging at the Fedora Project Community Corner. Shounak and I chuckled at the photograph shared by Yashwanth while we were on the way, since our punctuality from the day before might have most likely rubbed off on him. After a smooth ride, we soon arrived at the venue entrance at around 1030am Indian Standard Time. Given that we had the lay of the land and our posters were already placed properly, we had more time to conveniently set up our swagpacks and exhibits at our booth. I checked in with Matthew about how his preparations for his talk were going, while Shounak and Yashwanth started arranging the swagpacks and exhibits on the booth desk.


Collection C (Shounak Dey, CC BY-SA 4.0)
Samyak decided to add a couple more tricky questions to the question list of the Fedora Project Community Trivia. That was a brilliant idea since it allowed visitors from the previous day to go out of their way to explore more about the Fedora Project and its dealings. As we were quite economical with handing out swagpacks the day before, and none of us was in the mood for taking them back home, we decided to be rather generous that day. I devised a plan for handing out our limited-edition Fedora Project magnet-and-clip combo to the attendees entering Matthew's talk to appreciate their presence there, while Matthew contemplated whether he should extend his talk to include 35 Fedora Linux releases instead of the previously planned 30 of them, since he had to manage the talk duration.


Collection D (Shounak Dey, CC BY-SA 4.0)
As his talk was scheduled for 0115pm Indian Standard Time, we had more than enough time before then to attend to the visitors. We also decided to temporarily shut down the Fedora Project Community Corner for those 45 minutes to allow a larger audience to attend Matthew's presentation instead. Unfortunately, just like the day before, visitors continued to confuse our booth with the DevConf.IN registration desk. We had a frustrated Samyak craft a handwritten note at our booth to guide folks to the actual DevConf.IN registration desk. His frustrations were well placed, as even though we loved interacting with visitors, we would rather spend time and energy talking about the Fedora Project and Red Hat than being punished for the booth's attendance by becoming glorified compasses.


Collection E (Akashdeep Dhar and Shounak Dey, CC BY-SA 4.0)
A quick catch-up with Sudhir Dharanendraiah allowed me to remind him of the community dinner that we were planning to have later that day at Ishaara, Viman Nagar, and also share some Fedora Project stickers with him for them to be shared by the Red Hat India Communities booth personnel. That not only helped out the staff there, but it also allowed the Fedora Project to be cross-promoted across multiple co-located booths. Following this, I headed over next to the DevConf.IN registration desk to avail myself of a couple of DevConf.IN-themed magnets and clips. To return the goodwill, I also shared some Fedora Project magnet-and-clip combos with them to be shared by the visiting attendees, a gesture that they not only appreciated but that also allowed us to further pursue cross-promotion.


Collection F (Akashdeep Dhar and Shounak Dey, CC BY-SA 4.0)
At around 1200pm Indian Standard Time, Shounak and Yashwanth took off to explore the booths around DevConf.IN 2026, leaving Samyak and me to tend to the booth visitors. While the footfall did drop by the time they left, it slowly started picking up pace about fifteen minutes later, with questions around .NET compatibility in Fedora Linux and security developments in the Fedora Project. There was another wave of quiz participants who checked in with us about the Fedora Project Community Trivia answer keys and verified where they got things wrong. It was rather refreshing to see that while there were a few visitors who were argumentative about their defeat, a greater number embraced getting to know the things that they did not previously know about the Fedora Project and its dealings.


Collection G (Akashdeep Dhar and Shounak Dey, CC BY-SA 4.0)
One of the learnings we took away from organising an interactive event that made the best use of visitors being there in person was to order more exclusive swagpacks in the future. With Samyak dropping another handcrafted note to inform visitors about the temporary shutdown and me wrapping things up at the booth desk, we were pleasantly surprised by Sayak Sarkar, who managed to make it to the venue early that day. Samyak set up a countdown timer on his iPad placed on the booth desk to expire at around 0100pm Indian Standard Time to let folks know the same. After a quick catch-up with both Sayak and Deepesh Nair, we had the returning Shounak and Yashwanth haul the swagpacks and exhibits to the first floor's VY0104 room, where Matthew's talk was scheduled to be organised.

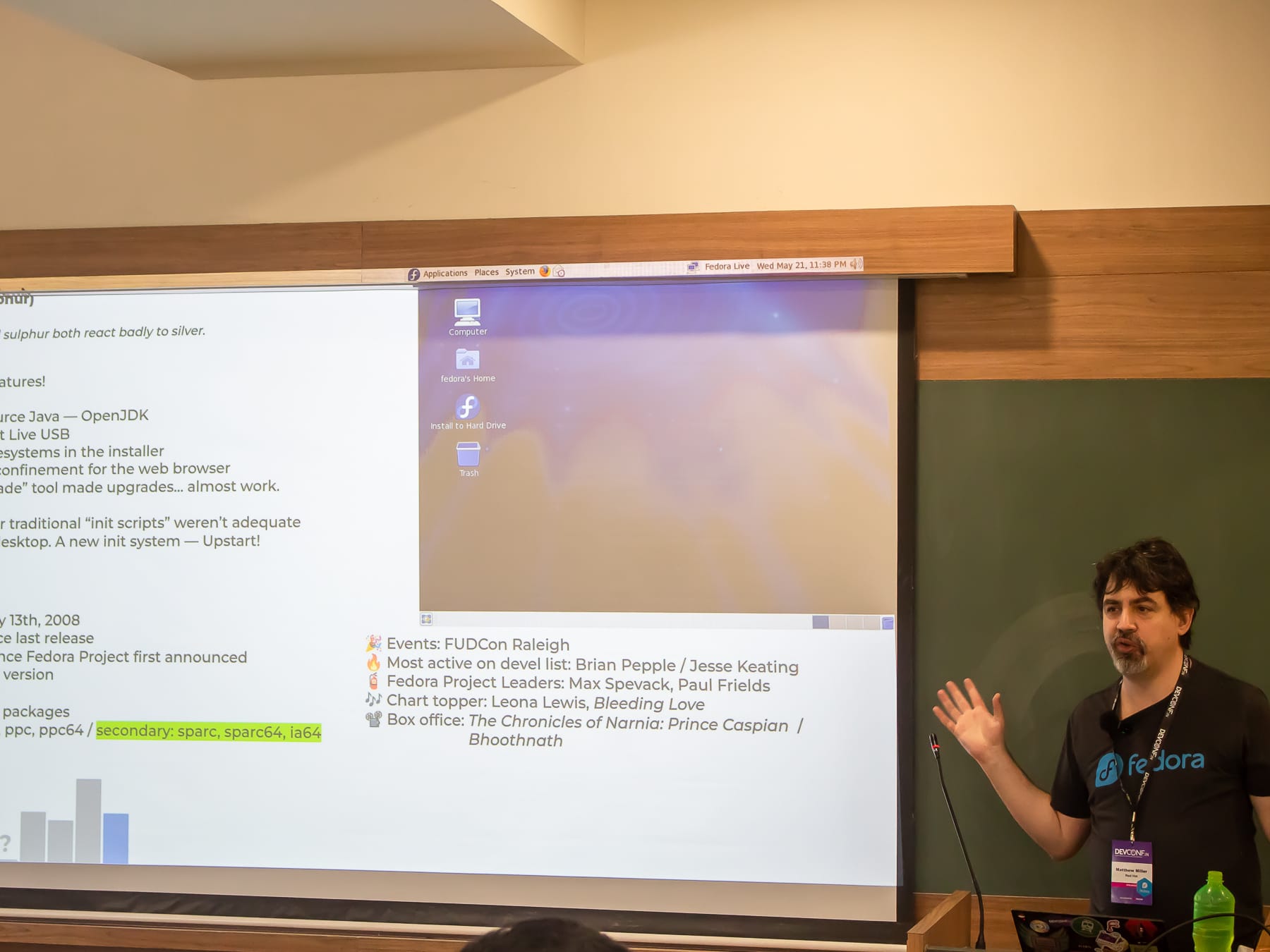
Collection H (Shounak Dey, CC BY-SA 4.0)
As Matthew was getting prepared for the talk, Shounak made his way to the elevated back of the room with his fancy Canon DSLR camera. Yashwanth and I worked on arranging the swagpacks on one of the front desks so that attendees could help themselves. The room was soon filled to the brim, and the talk went well, albeit with some minor considerations, with Matthew having to speed up the delivery toward the end to accommodate five more releases. Matthew also ensured that there was some time left at the end for questions and feedback; a bunch of them were related to artificial intelligence, his experience, changing times, and newer responsibilities. With the talk getting wrapped up at around 0200pm Indian Standard Time, the Fedora Project Indian Crew made it back to the ground floor.


Collection I (Akashdeep Dhar and Shounak Dey, CC BY-SA 4.0)
We had to wash our plans of having lunch at around that time down the drain since the booth activities were planned to wrap up earlier that day. That would have essentially meant that we had to be around to declare the winners of the second day of the Fedora Project Community Trivia at around 0230pm Indian Standard Time. Samyak made himself busy populating the scores on the raffle service while Shounak unsuccessfully tried sharing the progress on the Fedora Badges Revamp Project with Sayak. The poor cellular data reception, along with the wireless downtimes, made it extremely difficult for us to connect to the outside world. Yashwanth and I instead decided to field other conversations around the use of Fedora Linux in the robotics field and other adjacent infrastructure uses.


Collection J (Shounak Dey, CC BY-SA 4.0)
Matthew joined us soon, asking for feedback, and I shared that it would have been best to cover the earlier releases quickly while spending more time on the recent ones, because it was his personal experience as the Fedora Project Leader that people were there for. Since we coincidentally had him around then, it just made sense for him to felicitate the lucky winners with the exclusive Fedora Project-themed sippers. With Kashyap Ekbote helping us with the pictures after we were through with the awarding ceremony, Rajan Shah appreciated us for putting up a great show of community engagement at the conference. At around 0330pm Indian Standard Time, we started wrapping up our booth operations, with many enthusiastic visitors returning to express just how much they liked us there.


Collection K (Akashdeep Dhar, CC BY-SA 4.0)
Samyak and I went around reminding Matthew and Sayak about the dinner that he had booked previously in the morning, before seeing them off. For the late lunch, though, Shounak and Samyak discovered the La Sicilia Bistro and Patisserie restaurant, which was barely under five kilometres away from the event venue. On our way out, we swiftly got ourselves some photographs at the DevConf.IN 2026 event entrance was before we booked an Uber ride to the meal place. While the likes of Sudhir and Kashyap could not join us for lunch, Avadhoot Dhere gracefully joined our little party, and we did end up having quite the delicacies while sharing the best moments of the day. We saw each other off at around 0500pm Indian Standard Time after a rather late lunch and returned home on a quiet Uber ride.


Collection L (Akashdeep Dhar, CC BY-SA 4.0)
Having had a brief respite, one hell of a confusing disaster struck when I checked with Sudhir to restate the location of the restaurant. It turned out that Samyak had prebooked the wrong branch of the Ishaara restaurant, which was about thirty kilometres on the outskirts of the city, i.e., in Wakad and not the one that was under approximately ten kilometres from all ends, i.e., in Viman Nagar. I checked in with Samyak, but after not hearing back from him, I decided to create a new booking under my name amidst the filled capacity due to the Valentine's Day evening. Thankfully, I was able to get one, and after hearing from Matthew and Karen Miller about them having gone to the wrong location, I asked them to go on without us because it would have taken at least a couple of hours just to get there.


Collection M (Akashdeep Dhar, CC BY-SA 4.0)
Even Samyak had to tap out since he was feeling under the weather after all the work from the day, so I checked in with the likes of Shounak, Yashwanth, and Sudhir to reconfirm the correct location at around 0730pm Indian Standard Time. It was quite the mess-up, but I was not going to let the Fedora Project's community presence at DevConf.IN 2026 end on a sour note. The four of us ordered light bites with hand gestures, as the restaurant employed specially-abled people, and it was an enlightening experience to witness the world from their perspective. After some interesting conversations and unpacking catchups, Sudhir and Yashwanth left first before Shounak and I were able to find ourselves an Uber ride, finally breathing a sigh of relief after having organised this throughout the last couple of long days.
05 Mar 2026 6:30pm GMT
04 Mar 2026
 Fedora People
Fedora People
Peter Czanik: New toy: Installing Fedora Linux on the HP Z2 Mini
04 Mar 2026 11:56am GMT
Tim Waugh: Logsqueak: Rescuing Insights from the Logseq Journal
I've been using Logseq for a year now and it's become the backbone of my workflow. I have pages dedicated to specific topics, concepts, projects, meetings… all sorts of things.
During my day, when I want to note something down or write something out to think about it, the daily Logseq journal is the obvious place for it to go. It has been an invaluable habit to build. But there's a catch: the journal can easily become a black hole. It ends up as a chaotic mix of meeting notes, fleeting thoughts, random ideas, task lists and the occasional moment of genuine insight.
Most of the time, I try to link journal items to the relevant pages. Sometimes I remember to update those pages in light of new information. But other times I forget, and those insights get buried in the timeline, only resurfacing if I explicitly search for them.
All of those things belong in the journal, but some of them also belong in permanent pages. I wanted a way to filter the signal from the noise and capture things that I can integrate into my pages, in a way that makes them traceable back to the journal, without leaving the keyboard.
Enter Logsqueak: a proof-of-concept experiment to see if a local AI model can act as an automated gardener for a Personal Knowledge Management (PKM) system.

How Logsqueak Works
It's a Python-based terminal UI built with Textual, using RAG (Retrieval-Augmented Generation) via Ollama. Because PKM data is highly personal, my aim was to be able to build a tool that can run entirely on a local GPU, meaning your private journal entries never have to leave your machine. (Though you can certainly connect it to much larger cloud models if you prefer.)
The workflow is broken down into 3 phases:
1: Extraction (Signal vs. Noise)
In this phase, Logsqueak reads your Logseq journal and helps identify which items are ephemeral daily noise (e.g., "Morning standup at 9am") and which are actual knowledge or insight worth keeping.
2: Refinement (Making it Evergreen)
Temporal context is stripped away, and additional context from parent bullet points is added in.
- Original Journal Entry:
- Working on the new analytics dashboard
- Finally figured out why the main chart was double-fetching data on load. The
useEffecthook was missing the empty dependency array.
- Finally figured out why the main chart was double-fetching data on load. The
- Working on the new analytics dashboard
- Logsqueak Refinement:
- To prevent double-fetching data on load in the analytics dashboard, ensure the
useEffecthook for the main chart includes an empty dependency array.
- To prevent double-fetching data on load in the analytics dashboard, ensure the
3: Integration (Filing it Away)
In this final phase, the most semantically relevant pages in your Logseq graph are tracked down, and the best insertion point is identified. Logsqueak will suggest exactly which page and heading the new insight belongs under.
Logseq is built around powerful block properties, so crucially this is where the traceability happens. When an insight is integrated, Logsqueak adds an extracted-to:: property to the original journal block, linking it directly to the new block. The new block on the target page gets an id:: property linking back. This means you can always jump from your polished knowledge base straight back to the original journal entry to see the full context of what you were doing that day.
All writes are performed using a custom engine specifically built for Logseq's Markdown format, ensuring your notes stay safe. Because this is a proof-of-concept, all writes are guarded by explicit user approval-Logsqueak won't change your files without you saying "yes."
Try it out!
Logsqueak requires Python 3.11+ and an AI assistant. You can use Ollama to run everything locally.
If you're on Fedora, getting the prerequisites running is incredibly straightforward. Since Fedora Workstation ships with recent Python versions out of the box, you're already halfway there. You just need to grab Ollama to run the models locally, set up a virtual environment, and you're good to go:
# Assuming you've installed Ollama
git clone https://github.com/twaugh/logsqueak.git
cd logsqueak
./setup-dev.sh
source venv/bin/activate
logsqueak initTaming the Knowledge Graph
This tool can help you turn a pile of daily logs into a structured, searchable knowledge base. Although it can't yet create new pages from scratch or be given custom instructions about how best to integrate things into the graph, it's already useful enough for me to use in my daily routine.
It's very much a proof-of-concept though, and I'd love to get some feedback from other developers and knowledge management enthusiasts. You can check out the code on GitHub.
Building Logsqueak made me realise just how much time I spend thinking about note-taking friction. While Logsqueak handles my fast, keyboard-driven daily logging, I actually do a lot of my deep thinking away from the screen on a Ratta Supernote e-ink tablet.
I recently found myself trying to solve a similar "black hole" problem over there. The result is Slipstream: a Zettelkasten framework to let you build infinitely nested idea networks by hand.
If you happen to be an e-ink user who prefers a stylus to a keyboard when you need to disconnect and focus, you might find it an interesting contrast. As a bonus, because Slipstream has a structured convention, exporting those handwritten notes to plain text makes them perfectly readable for the exact kind of LLM processing Logsqueak relies on. It's analogue thinking, ready for the AI age.
The post Logsqueak: Rescuing Insights from the Logseq Journal appeared first on PRINT HEAD.
04 Mar 2026 11:30am GMT
Peter Czanik: Syslog-ng 4.11.0 packaging status
04 Mar 2026 8:31am GMT
03 Mar 2026
 Fedora People
Fedora People
Avi Alkalay: Uniqlo T-Shirt Bash Script Easter Egg
At Uniqlo flagship store in Ginza, Tokyo, there was this T-shirt with an encoded shell script.


Well, I had to decode it and see the result.
I took a photo with my iPhone and used its own OCR, which made a lot of confusion between 0 (zero), O (capital o) and 8, mixed 1 and l (small L), and yielded many chars as very similar glyphs but in advanced Unicode ranges, which are invalid for Base64 encoding. It took me some time to fix it all. The final corrected text is this:
#!/bin/bash
eval "$(base64 -d <<< 'IyEvYmluL2Jhc2gKCiMgQ29uZ3Jhd
HVsYXRpb25zISBZb3UgZm91bmQgdGhlIGVhc3RlciBlZ2chIOKdpO+4jwojIOOBiuO
CgeOBp+OBqOOBhuOBlOOBluOBhOOBvuOBme+8gemaoOOBleOCjOOBn+OCteODl+OD
qeOCpOOCuuOCkuimi+OBpOOBkeOBvuOBl+OBn++8geKdpO+4jwoKIyBEZWZpbmUgd
GhlIHRleHQgdG8gYW5pbWF0ZQp0ZXh0PSLimaVQRUFDReKZpUZPUuKZpUFMTOKZpV
BFQUNF4pmlRk9S4pmlQUxM4pmlUEVBQ0XimaVGT1LimaVBTEzimaVQRUFDReKZpUZ
PUuKZpUFMTOKZpVBFQUNF4pmlRk9S4pmlQUxM4pmlIgoKIyBHZXQgdGVybWluYWwg
ZGltZW5zaW9ucwpjb2xzPSQodHB1dCBjb2xzKQpsaW5lcz0kKHRwdXQgbGluZXMpC
gojIENhbGN1bGF0ZSB0aGUgbGVuZ3RoIG9mIHRoZSB0ZXh0CnRleHRfbGVuZ3RoPS
R7I3RleHR9CgojIEhpZGUgdGhlIGN1cnNvcgp0cHV0IGNpdmlzCgojIFRyYXAgQ1RS
TCtDIHRvIHNob3cgdGhlIGN1cnNvciBiZWZvcmUgZXhpdGluZwp0cmFwICJ0cHV0I
GNub3JtOyBleGl0IiBTSUdJTlQKCiMgU2V0IGZyZXF1ZW5jeSBzY2FsaW5nIGZhY3R
vcgpmcmVxPTAuMgoKIyBJbmZpbml0ZSBsb29wIGZvciBjb250aW51b3VzIGFuaW1hd
Glvbgpmb3IgKCggdD0wOyA7IHQrPTEgKSk7IGRvCiAgICAjIEV4dHJhY3Qgb25lIGN
oYXJhY3RlciBhdCBhIHRpbWUKICAgIGNoYXI9IiR7dGV4dDp0ICUgdGV4dF9sZW5nd
Gg6MX0iCiAgICAKICAgICMgQ2FsY3VsYXRlIHRoZSBhbmdsZSBpbiByYWRpYW5zCiA
gICBhbmdsZT0kKGVjaG8gIigkdCkgKiAkZnJlcSIgfCBiYyAtbCkKCiAgICAjIENhb
GN1bGF0ZSB0aGUgc2luZSBvZiB0aGUgYW5nbGUKICAgIHNpbmVfdmFsdWU9JChlY2
hvICJzKCRhbmdsZSkiIHwgYmMgLWwpCgogICAgIyBDYWxjdWxhdGUgeCBwb3NpdGl
vbiB1c2luZyB0aGUgc2luZSB2YWx1ZQogICAgeD0kKGVjaG8gIigkY29scyAvIDIpIC
sgKCRjb2xzIC8gNCkgKiAkc2luZV92YWx1ZSIgfCBiYyAtbCkKICAgIHg9JChwcmlu
dGYgIiUuMGYiICIkeCIpCgogICAgIyBFbnN1cmUgeCBpcyB3aXRoaW4gdGVybWluY
WwgYm91bmRzCiAgICBpZiAoKCB4IDwgMCApKTsgdGhlbiB4PTA7IGZpCiAgICBpZi
AoKCB4ID49IGNvbHMgKSk7IHRoZW4geD0kKChjb2xzIC0gMSkpOyBmaQoKICAgICM
gQ2FsY3VsYXRlIGNvbG9yIGdyYWRpZW50IGJldHdlZW4gMTIgKGN5YW4pIGFuZCAyM
DggKG9yYW5nZSkKICAgIGNvbG9yX3N0YXJ0PTEyCiAgICBjb2xvcl9lbmQ9MjA4CiA
gICBjb2xvcl9yYW5nZT0kKChjb2xvcl9lbmQgLSBjb2xvcl9zdGFydCkpCiAgICBjb
2xvcj0kKChjb2xvcl9zdGFydCArIChjb2xvcl9yYW5nZSAqIHQgLyBsaW5lcykgJSBj
b2xvcl9yYW5nZSkpCgogICAgIyBQcmludCB0aGUgY2hhcmFjdGVyIHdpdGggMjU2L
WNvbG9yIHN1cHBvcnQKICAgIGVjaG8gLW5lICJcMDMzWzM4OzU7JHtjb2xvcn1tIiQ
odHB1dCBjdXAgJHQgJHgpIiRjaGFyXDAzM1swbSIKCiAgICAjIExpbmUgZmVlZCB0b
yBtb3ZlIGRvd253YXJkCiAgICBlY2hvICIiCgpkb25lCgo= ')"When base64-decoded, this bash script appears:
#!/bin/bash
# Congratulations! You found the easter egg! ❤
# おめでとうございます!隠されたサプライズを見つけました!❤
# Define the text to animate
text="♥PEACE♥FOR♥ALL♥PEACE♥FOR♥ALL♥PEACE♥FOR♥ALL♥PEACE♥FOR♥ALL♥PEACE♥FOR♥ALL♥"
# Get terminal dimensions
cols=$(tput cols)
lines=$(tput lines)
# Calculate the length of the text
text_length=${#text}
# Hide the cursor
tput civis
# Trap CTRL+C to show the cursor before exiting
trap "tput cnorm; exit" SIGINT
# Set frequency scaling factor
freq=0.2
# Infinite loop for continuous animation
for (( t=0; ; t+=1 )); do
# Extract one character at a time
char="${text:t % text_length:1}"
# Calculate the angle in radians
angle=$(echo "($t) * $freq" | bc -l)
# Calculate the sine of the angle
sine_value=$(echo "s($angle)" | bc -l)
# Calculate x position using the sine value
x=$(echo "($cols / 2) + ($cols / 4) * $sine_value" | bc -l)
x=$(printf "%.0f" "$x")
# Ensure x is within terminal bounds
if (( x < 0 )); then x=0; fi
if (( x >= cols )); then x=$((cols - 1)); fi
# Calculate color gradient between 12 (cyan) and 208 (orange)
color_start=12
color_end=208
color_range=$((color_end - color_start))
color=$((color_start + (color_range * t / lines) % color_range))
# Print the character with 256-color support
echo -ne "\033[38;5;${color}m"$(tput cup $t $x)"$char\033[0m"
# Line feed to move downward
echo ""
doneThe original encoded text, when executed in my Linux terminal gives a beatiful animation, similar to this:

After decoding and executing the script, I found other people doing the same:
- Uniqlo's Peace For All Easter Egg | leewc
- GitHub - SeenamZaSodaSingha/UNIQLO_Akamai_TShirt_Base64 · GitHub
But I swear I decoded it myself first, without any help.
03 Mar 2026 9:18pm GMT
Akashdeep Dhar: Fedora Project Community Corner @ DevConf.IN 2026 - Day One

As the event owner for the Fedora Project's community presence during the DevConf.IN 2026 conference, I had to ensure that I made it to the event venue as early as possible. The first day began with me getting ready by 0930am Indian Standard Time since I had returned from meeting the likes of Samyak Jain, Matthew Miller and Karen Miller late the day before. I had to put a pin on my plans to check the inventory of the swag packs that I had delivered at Shounak Dey's house, as it was quite the struggle to get us Uber rides to the MIT World Peace University campus, Kothrud. While checking with Yashwanth Rathakrishnan, I also ensured that I packed the essential tooling that might come in handy while establishing and tearing down our booth at the DevConf.IN venue.


Collection A (Akashdeep Dhar, CC BY-SA 4.0)
After a couple of Uber cab cancellations, Shounak and I were finally on our way from Chandan Nagar to Kothrud. We seemed to have greatly underestimated the time it would take for us to get there, as not only was it thirty kilometres away from us, but the morning office-going traffic was also at its peak. We projected that it would take us around an hour to get there, but since the booth activities were to begin from 1100am Indian Standard Time onwards, we had ample time in our hands. I checked in with Yashwanth and Samyak on our organiser chatroom, who had reached there by around 1000am Indian Standard Time. They had joined the queue to pick up their badges and swag packs from the organiser's desk, and also went ahead to visit where our Fedora Project Community Corner was located.


Collection B (Akashdeep Dhar, CC BY-SA 4.0)
To both Shounak's and my chagrin, we figured out a little too late that the venue had been moved to the newly constructed Vyas Building of the MIT World Peace University campus. We realised it after our (rather friendly) Uber driver dropped us off, so the two of us had to walk around a kilometre hauling the heavy swag boxes and booth equipment. I did connect with Yashwanth and Samyak so that they could help carry those over from the entrance, but there must have been a disconnect, as Shounak and I had to sweat our way into the Vyas Building anyway. After passing a security check and a flight of wide stairs, our relief came in the form of one patient, Avadhoot Dhere, whom we met at the building's entrance, who helped us carry our load to the Fedora Project Community Corner location.


Collection C (Akashdeep Dhar, CC BY-SA 4.0)
At around 1030am Indian Standard Time, we had about thirty minutes to get our community booth set up with exhibits and swag packs. I delivered a quick briefing to our on-site Fedora Project Indian Crew on what was expected of them and how they had to abide by the DevConf.IN Code of Conduct, when to take breaks after duly informing about the same, and how judicious they have to be regarding the swag distribution. We started drawing quite a huge crowd of early visitors to the booth while we were busy setting up the community booth, a bunch of whom confused our location with the registration desk. Huge kudos to Rajan Shah, who helped us secure a strategic location to allow for most (if not all) community conversations to come to us first before they seeped into other booths.


Collection D (Akashdeep Dhar, CC BY-SA 4.0)
While Samyak and Shounak got busy setting up the A3-sized posters that I had previously designed, Yashwanth and I worked on organising the swag stickers and swag magnets on our booth desk. I briefly paused to take in just how amazing a task the DevConf.IN 2026 organising committee did with arranging the booth backdrops and positioning the two desks at a right angle for us. With Samyak's handspan calculations and Shounak's accurate pasting, we soon had our four posters on topics like Matthew's presentation, Flock To Fedora 2026, DevConf.IN 2026's Fedora Badge and Fedora Project Community Trivia, ready to go. Since we had visitors lining up already before the scheduled beginning, we had to double-time addressing the people and setting up our Fedora Linux-powered laptops.


Collection E (Shounak Dey, CC BY-SA 4.0)
By around 1100am Indian Standard Time, we had already addressed approx 200 visitors at the booth, so you could imagine just how difficult the opening hours were for the on-site Fedora Project Indian Crew to handle that wave. Our economical yet outgoing approach towards handing out our limited swag packs allowed us to pace ourselves while dealing with a huge number of attendees. To add to that, our inclusive demeanour towards the visitors allowed them to bring their conversations and feedback about Fedora Linux and/or the Fedora Project to us. While the population numbers did not hold a candle against the likes that we usually get in places like FOSDEM, I extended those experiences to ensure that we did not stretch ourselves thin while answering questions and receiving feedback.


Collection F (Akashdeep Dhar, CC BY-SA 4.0)
We were also visited by Dorka Volavkova, who checked in with me about the situation regarding the availability of swag packs at our booth. While I was initially dependent on folks portering in swag packs from various other events due to logistical difficulties, I soon realised that the plan was not reliable. I informed her about my decision to extend the Fedora Mindshare budget request by about USD 150 to ensure that I could produce the swag packs locally with Rajan's and Devang Parikh's assistance. This not only allowed for deterministic representation at DevConf.IN 2026, but the same resources could also be used for organising more such Fedora Project events around India or APAC. Dorka was happy to note that we followed an ideal process of getting swag packs for events from local vendors.


Collection G (Shounak Dey, CC BY-SA 4.0)
As the footfall slightly slowed down, Shounak and I took that opportunity to leave for the registration desk to pick up our badges and swag packs. It had literally escaped our minds since we were occupied with setting up the Fedora Project Community Corner, but we did manage to get our DevConf.IN-themed backpack and ID badges on time. We fielded various questions from visitors wanting to know about what the Fedora Project is, how Fedora Linux differs from other distributions, how Fedora Linux shapes the future of enterprise distributions, and what one can do to get started with contributing. Yashwanth suggested rewarding more interesting conversations with our limited-edition Fedora Project magnet-and-clip combo, and that helped us drive the course of our conversations and shape an open narrative.


Collection H (Shounak Dey, CC BY-SA 4.0)
Matthew soon arrived at around 1200pm Indian Standard Time, and that not only gave us one more person to field interactions with, but the visitors could also avail themselves of the historical context about the Fedora Project that he could offer, having served in the Fedora Project Leader position for over a decade. This was also our opportunity to gather folks around us and promote his talk about "30/35 Fedora Linux Releases in 30/35 Minutes", which was scheduled for the next day. The younger, college-going crowd looked up to us for working on free and open source software as our full-time employment and wanted to understand how they could begin doing the same. This was a great opportunity for us to showcase our onboarding pathways into the community through the Fedora Join SIG.


Collection I (Shounak Dey, CC BY-SA 4.0)
Among the curious questions that I fielded, a couple that I remember had to do with the incompatibility of Fedora Linux as a student base operating system for attempting CNCF certification examinations and the apparent lack of a long-term release in the Fedora Linux offerings. While I personally did not have any experience with those examinations, I elaborated on how Fedora Linux's focus on innovation and the fast-moving release cycle could be something that could not be conveniently kept up with by the examination proctors. As for the question about the Fedora Linux long-term distribution release, I recommended that they use CentOS Stream and/or the Red Hat Enterprise Linux Developer Subscription for more serious workloads that require strict quality and uncompromising support.


Collection J (Shounak Dey, CC BY-SA 4.0)
As I was wearing a CentOS Linux-themed tee, I was also able to steer discussions into explaining how the Fedora Project's decisions around technologies such as the systemd movement, PipeWire inclusion, Wayland defaults, etc., were seen as controversial in the past but ended up becoming industry standards just a couple of years later. I wanted our conversations with the visitors to be a gateway through which they could start exploring the space of open source enterprise distributions and potentially begin contributing to the projects of their interest. Amidst our conversations, the visitors were drawn to the Fedora Project Community Trivia that Samyak helped craft questions for, and the fact that it had an exclusive Fedora Project-themed sipper as an award prize only helped us farm more engagement.


Collection K (Akashdeep Dhar and Shounak Dey, CC BY-SA 4.0)
Shounak stayed busy photographing with his fancy Canon DSLR camera as we guided visitors to scan the QR code on our posters to do things like get themselves the associated Fedora Project event badge, learn more about the annual flagship contributor conference, Flock To Fedora 2026, and, of course, participate in the Fedora Project Community Trivia. A bunch of these visitors had experience using a GNU/Linux distribution, and with us sharing just how Fedora Linux allows them to build solutions for the consumers of today and tomorrow, with its packages being on the leading edge, they were eager to try it out on their personal devices. There were comparison conversations against the likes of Microsoft Windows and Apple macOS, too, on a more superficial level, among the younger folks there.


Collection L (Shounak Dey, CC BY-SA 4.0)
A DevConf.IN volunteer, Rahul Sharma, visited our booth to inform us about the catering being served on the eighth floor of the building at around 0100pm Indian Standard Time. Right around this time, we had a confusing conflict with a fellow speaker or booth participant who we found to be taking away Shounak's swag pack, claiming it to be theirs since they had left it there for the restroom. While we could not verify the truthfulness of their claim, I sternly asked them to return the swag pack to Shounak and verify with his friends before pressing further. Since he did not bother informing any of the booth staff about leaving behind his objects, we could not be held responsible for any misplaced belongings. For all that trouble, it turned out that his friend indeed had his swag pack with him all along.


Collection M (Shounak Dey, CC BY-SA 4.0)
After reporting this awkward incident to an adjacent DevConf.IN volunteer, Shounak and I decided to head upstairs for lunch. With Matthew leaving, it was down to the four of us handling the booth, so we wanted to ensure that the booth was staffed by at least a couple of folks at any given time. Since both Samyak and Yashwanth mentioned that they were not feeling hungry enough, the two of us decided to scale through sixteen flights of stairs to make it to the eighth floor. It is not that the place did not have elevators, but they were jam-packed, and we would have ended up wasting time waiting for a vacant one to become available, given how popular DevConf.IN 2026 ended up being in terms of attendee count. We also connected with Avadhoot to check on his experience at the conference so far.


Collection N (Shounak Dey, CC BY-SA 4.0)
We did end up wasting our time, though, since we found a huge queue on the eighth floor at the dining establishment serving volunteers, speakers and staff. Actually, scratch that, it was not entirely a wasteful endeavour because I got to meet up with Brian Proffitt, whom I met after almost a year or so since the previous DevConf.IN. After a brief catch-up and a bio break, the two of us headed back to the booth, since waiting in the queue doing absolutely nothing before spending more time to have food would have been wasteful. Instead, Shounak and I decided to go across the place to see what other booths had to offer, which led me to meet a bunch of community friends and fellow employees. We met Sudhir Dharanendraiah while we were exploring, meeting after almost a couple of years.


Collection O (Akashdeep Dhar, CC BY-SA 4.0)
He remarked that the booth personnel from the Red Hat India Communities ran out of their swag during the first few hours of the event's commencement and praised how we kept visitors engaged throughout the day. He also said that not combining the Fedora Project community booth with the Red Hat India Communities was the right call, since that allowed us to be crystal clear in our messaging that the Fedora Project and Red Hat do indeed care about India and APAC users and contributors. We were even asked whether we had a regional community presence or meetup cadence, which gave us something to explore and consider from the Fedora Mindshare activity perspective. The two of us finally came back to the booth, letting Samyak and Yashwanth head away for lunch.


Collection P (Akashdeep Dhar, CC BY-SA 4.0)
The other major questions and feedback that came to us about Fedora Linux had to do with what we were planning to do around artificial intelligence. Being a Fedora Mindshare representative to the Fedora Council at the time, and also someone who proposed the creation of an AI-assisted contribution policy, I elaborated on how inclusive our community had recently become towards policy-abiding AI-assisted contributions. I also emphasised that with subprojects and SIGs around AI, ML, and PyTorch, our focus was to establish Fedora Linux as a general-purpose platform of choice for generalists, developers, sysadmins, or enthusiasts to build AI-powered technologies on, rather than have AI-based solutions that no one asked for enabled by default in our primary offerings.


Collection Q (Shounak Dey, CC BY-SA 4.0)
We met Pravin Satpute, who suggested that we have lunch at the cafeteria on the fifth floor, and after letting Samyak and Yashwanth return from their exploration, we headed there with Avadhoot. The dining choice was limited to a Vegetarian Biryani and Cold Coffee, but at around 0230pm Indian Standard Time, that felt like a divine serving. We were able to get ourselves an elevator this time around, and after a brief catch-up with the likes of Saumili Dutta and Kashyap Ekbote, both of whom I met previously during GNOME Asia 2024 in Bengaluru, we returned to the booth. I made it a point to remind the booth crew to stay hydrated now and then, given just how easy it could be for folks to forget about self-preservation after being overwhelmed by almost 600 visitors since we reached the conference.


Collection R (Shounak Dey, CC BY-SA 4.0)
Coincidentally, I met Harshavardhan Sharma from openSUSE, whom we had met in the past in another conference, along with Sahil Tah, a college senior from my alma mater. DevConf.IN 2026, did manage to bring like-minded individuals into one place, regardless of which industry they belonged to, showing that openness and innovation are indeed the way forward when it comes to technology. Rajan made a visit to the Fedora Project Community Corner around that time, and he admired how we kept visitors occupied while providing them with things to learn and swag to collect. We were also soon visited by the likes of Amita Sharma and Sudhir Menon, whom we caught up with after a long time, while offering them the warm embrace that the Fedora Project's "Friends" foundation is known for.


Collection S (Shounak Dey, CC BY-SA 4.0)
I was also briefly visited by some folks who thought that we had mistaken the answer keys in the Fedora Project Community Trivia, but to their surprise, those were made tricky on purpose. I provided them with the context of how I planned those deceptively difficult questions while emphasising that we wanted the four winners each day of the conference to feel special about their victory. Since I had procured eight limited-edition Fedora Project-themed sippers for the winners, the attendees not only had to exhibit their community knowledge by getting full marks but also had to be lucky enough to emerge victorious in a raffle. We wanted folks to return to the booth thirty minutes before closing time for the announcements.


Collection T (Akashdeep Dhar, CC BY-SA 4.0)
While Samyak worked on populating the raffle with the high scorers on his laptop, I checked with Sayak Sarkar, who was visiting DevConf.IN, just like the year before. As the Vyas Building gave us very poor cellular reception, it was incredibly challenging to point him in the correct direction, especially since, while the venue remained the same as the previous year, the actual location had moved. For their first experience manning a community booth, I could not help but watch from a distance just how well both Shounak and Yashwanth did as volunteer contributors as I waited for Sayak to turn up at the Fedora Project Community Corner. At around 0430pm Indian Standard Time, I caught up with Sayak and introduced him to the Indian Crew as the curious crowd started gathering for the results.


Collection U (Akashdeep Dhar, CC BY-SA 4.0)
With the four winners being announced and felicitated by both Samyak and me, the visitors cheered for the winners as well as for the exciting activity. We clicked a few more pictures with Matthew before he went on his way to attend the dinner with the DevConf.IN speakers, organisers, and members. While I was invited to the dinner as well on behalf of the Fedora Project, it made little sense to me not to go out with the hardworking Fedora Project Indian Crew instead. In one of the conversations with Sayak and Shreyank Gupta, I was pleasantly surprised to learn that Shreyank was also a fellow Bengali, since I had always interacted with him in either English or Hindi for the past five years or so. After a few more pictures were taken by Shounak at the booth, we decided to start wrapping things up for the day.


Collection V (Akashdeep Dhar, CC BY-SA 4.0)
We unfortunately had to send some visitors back, and ask them to return the next day, who wanted a demonstration of Fedora Workstation at our exhibits. We had more than half of the swag packs left in our inventory, even after giving away a huge number of them to be cross-shared by the Red Hat India Communities booth personnel. After taking an inventory of all the belongings we had with us, we started looking for Uber rides back home. While we left the posters behind on the backdrops, we decided to take everything else with us to avoid misplacing them. It took a while for that to be confirmed, but after Samyak and Yashwanth got theirs, Shounak and I got ours, and we decided to leave for our homes around 0530pm Indian Standard Time, since we planned to reconvene for dinner later that day.


Collection W (Akashdeep Dhar, CC BY-SA 4.0)
After a rather uneventful but lengthy Uber drive, Shounak and I made it back to our homes. The evening went quite smoothly, with a pre-booking for dinner done at Wasabi15 under my name and Samyak and Yashwanth arriving early by 0800pm Indian Standard Time. Using the budget that I had previously requested from my management, we were able to have a great time unpacking from a busy day running operations at the Fedora Project Community Corner. Yashwanth sought advice on how he could take his contributions further, and Shounak shared how he got started in free and open source software contribution. With some great Asian cuisine and even greater conversations, we called it a night at 1000pm Indian Standard Time and went back to our places to prepare for the next day.
03 Mar 2026 6:30pm GMT
Fedora Community Blog: Fedora Documentation translations not available from March 4th, 2026

Fedora Documentation translations will be put on hold from March 4th as the Fedora Localization Team has started the process of migration from pagure.io to the Fedora Forge. From the date, translation projects of the documentation (with 'fedora-docs-l10n' in name) will be gradually locked on the Fedora translation platform. Translation automation of the Docs website will also be stopped in the Fedora infrastructure. Consequently, there will be no translation updates available in the language versions on the Fedora Documentation.
The migration involves all repositories which support and ensure the availability of translations of the Fedora Documentation. There is no possibility the migration can be performed 'on the fly' as changes in the repositories, related scripts and continuous integration with the translation platform cannot be dealt with independently. Therefore the translation process of the Fedora Documentation is kept on hold.
We regrettably ask the Fedora contributors, our translation community, to pull back from translating of the Fedora Documentation and wait till the translation automation of the documentation is resumed again.
The progress of migration can be followed in the localization tracker as issue #52.
The post Fedora Documentation translations not available from March 4th, 2026 appeared first on Fedora Community Blog.
03 Mar 2026 10:00am GMT
Brian (bex) Exelbierd: Jekyll Reads: the tooling behind my reading list
Why I needed more than a social reading site
In Rediscovering Reading (Without the Social Media Part) I wrote about stepping away from scrolling and building a slower, more deliberate reading habit. Part of that shift was making my reading log public without tying it to a dedicated social network.
The mechanics behind that were simple but fussy: keep a YAML file up to date, copy and paste links from Open Library, remember to grab cover images, and wire everything into Jekyll templates for the reading page and sidebar. None of it was hard, but it was just annoying enough that I knew future‑me would start skipping updates.
I built Jekyll Reads to make that workflow tolerable.
What Jekyll Reads actually does
Jekyll Reads is a small collection of pieces designed around a single idea: keep all the book data in one _data/reading.yml file and let everything else be presentation.
The core pieces are:
- A shared Node.js library that talks to Open Library, picks a reasonable match, and produces a standard YAML snippet for a book
- A command‑line tool that lets you search for a book and print the YAML to stdout, with options for indentation and auto‑selecting results
- A Vim integration that shells out to the CLI and drops the YAML directly into your buffer at the right indentation level
- A Visual Studio Code extension that does the same thing from inside the editor, with a proper search UI and update checks for the extension itself
All of this is intentionally boring: no external Node dependencies, just the built‑in modules and a bit of glue. The point is to make it slightly easier to keep the reading list current than to let it drift.
How it shows up on this site
On this site, the source of truth is _data/reading.yml. Entries that are still in progress, finished, or abandoned are all represented there with the same structure. The YAML includes things like start and finish dates, a link to more information (usually Open Library), an optional cover image, and a free‑form comment.
That data feeds two places:
- The dedicated reading page, which separates currently‑reading, finished, and abandoned books and shows covers, dates, and comments
- A small sidebar block on the home page that surfaces what I am currently reading, so the log is visible without needing a whole post for every book
Jekyll Reads does not try to be a general bookshelf app. It just reflects what I am already doing: writing short notes in YAML and publishing them along with the rest of the site.
Design constraints and trade‑offs
I made a few deliberate choices that might look odd if you are used to larger toolchains:
- No external Node dependencies. The library and CLI only use built‑in modules like
httpsandreadline. That keeps installation simple and makes it easy to run in constrained environments. - Open Library as the primary data source. It provides book metadata, cover images, and stable URLs without requiring another account or scraping.
- Plain YAML as the storage format. A static
_datafile is easy to version, review, and back up. It also plays nicely with Jekyll's existing data pipeline. - Multiple small tools instead of one big one. The CLI, Vim integration, and VS Code extension all sit on top of the same library, so they stay in sync without each re‑implementing the logic.
If any of that stops being true in the future, I can replace or extend the pieces without touching the core data file.
If you want to use it
The repository README walks through how to set up your own _data/reading.yml, wire up a reading page and sidebar, and use the CLI or editor integrations. It is written so that you can follow it even if you are not using the same Jekyll theme I am.
The code is MIT‑licensed and shipped under Electric Pliers LLC. If you want a lightweight way to publish a reading log without standing up a whole social network, you might find it useful.
You can find the repository and full documentation here: https://github.com/ElectricPliers/jekyll-reads
03 Mar 2026 7:50am GMT
